Internet has become an indelible part of our lives. We can’t really imagine a day without an internet device in our hands. It can be synonymous to oxygen now, we breathe internet, we sustain on it. With the course of time, it has become more accessible and affordable and therefore, everything has become digitized.
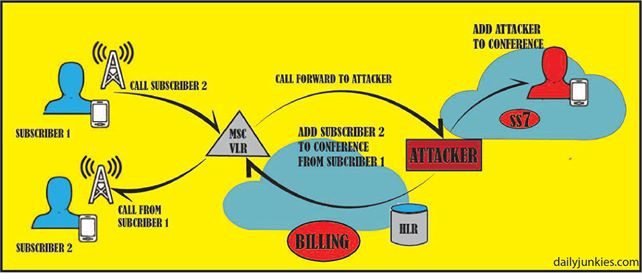
Since, everything good comes with some flaws attached to it, we must be aware of the unknown risks attached to the boon called ‘Internet’. As the internet is becoming more accessible and faster, the rate of cybercrime is also increasing at a proportionate rate. Cybercrimes are the crimes conducted online. They are meant to harm people accessing the internet. Cybercrimes are difficult to solve because the criminal sits behind a screen, hiding its identity. This blog is about SS7 attacks, to educate our readers about how they can destroy ones privacy. SS7 is the most common way of hacking in today’s date. Know about How hacker use SS7 hacking techniques at dailyjunkies.
Cybercrimes are at a rise because people are not yet aware about cyber security. In a cybercrime, the attackers just sit in a room, use a computer and access the internet to steal your money from banks or anywhere else. The attackers have become so advanced that they can locate you from any corner in the world and then threaten you or even leak your sensitive or private information. There are many methods through which the attacker can attack you.
Following are some commonly used attacks:
- SS7 Attack(Signaling System 7)
- Buffer overflow Attack
- SQL Injection
- Social Engineering
- MITM(Man-in-the-middle) Attack
There are more attacks also but these are the most commonly used attacks. In the list given above, MITM (Man-in-the-middle) attack is the most famous and widely used attack because it is easy and can be done by beginners also. It is effective most of the times.
Here are some points about the MITM attack : how you can avoid it and how does it work.
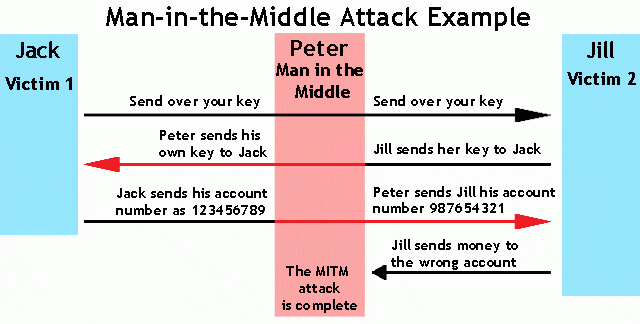
How you can be hacked without being knowing
MITM stands for Man in the Middle, the ‘man’ in the middle is important in this attack. The attacker becomes the middle men between your connections to the other device. Due to which you’re all the information, chats, call can be intercepted by the attacker. When you are connected to the internet the data from your device is sent and received directly from the internet servers. In MITM, the attacker intercepts your connection and becomes the middleman, the data now is transferred to the internet through the attacker that means the attacker can watch what you are doing on net, read your chats, see which sites you are visiting, etc.
How you can prevent Man in the middle attack?

Read Also How to stop DDoS attacks: 6 tips for defending against DDoS attacks
MITM attack gives the power to an attacker to read and write your information without your notice. Now one must ponder over, how can we stop or do anything to prevent it. Prevention can only take place, when one knows that they are being attacked. But you can prevent this to a large extinct just by taking a few steps.
Following are the steps that you can follow:
- Avoid using free or open Wi-Fi
- Avoid entering your credentials to a less secured website or connection.
- Avoid downloading applications from untrusted sources.
- Avoid using untrusted or unsafe web browser for your confidential work.
By taking these steps in mind, you can prevent yourself from the MITM attack to a large extent.
Read Also 8 tips on how to protect your site from hackers
Tech content on this site may include contributed articles and partnerships with industry voices. Learn more in our Editorial Policy.




